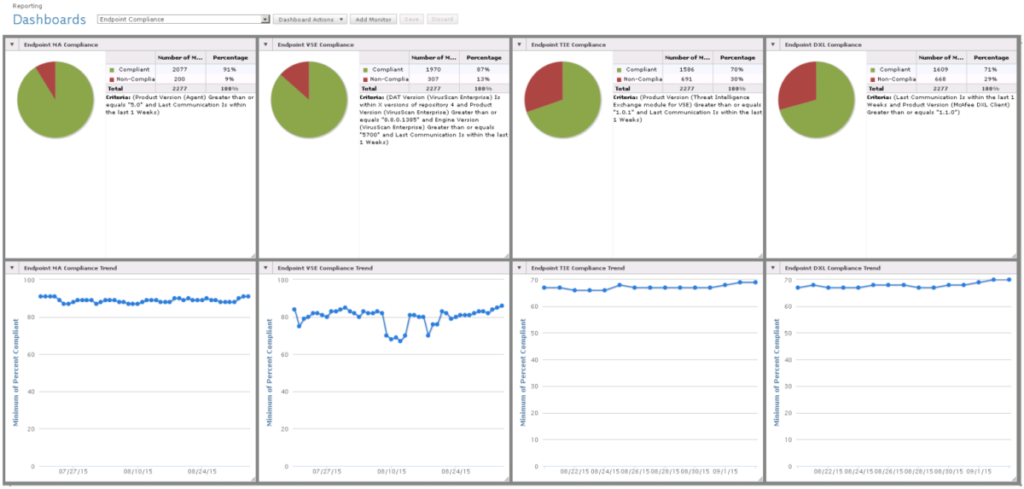
In our previous post about endpoint security, we discussed Operational Compliance, high-level metrics regarding coverage and timely communications. Now we're going to dive into the technical details of protection. Do note that depending upon the particulars of your endpoint protection, product-specific capabilities and functions will vary.
First let's consider your tools' configuration, settings, or tasks - collectively we'll just call policies. Ideally your management console can indicate that their policies are up to date and even a policy version. If your console does not have this ability, hopefully the local app's console can indicate this. Without some method to confirm that your apps are doing what they are being told, you have nothing more than assumption of what is in place.
- % of endpoints with up to date policies*
* Overall health is important but able to drill down into the details of any out of compliance systems so that they can be remediated.
If your chosen tool uses content updates e.g. signatures, .DAT files, engines, you will want to ensure that your endpoints are kept up to date. With most vendors releasing content on a daily basis, a good rule of thumb is ensuring that your systems are never more than four versions out of date. This threshold allows for reporting delays i.e. if a system is out of the office but online and also if systems are offline. For scanning engines or other content which are not updated as frequently, sticking with no less than a one version difference is good.
- % of endpoints with content within n-4 versions
- % of endpoints with engines within n-1 versions
These three aforementioned metrics are good, point-in-time snapshots. To really understand your environment, we recommend tracking these over time i.e. collect trends. Ideally your management consoles can be customized to display all of these in one screen, providing you with an at-a-glance view of the health of your organization.
- 30-day/90-day Trend % of endpoints with up to date policies
- 30-day/90-day Trend % of endpoints with content within n-4 versions
- 30-day/90-day Trend % of endpoints with engines within n-1 versions
Tracking trends is an effective way to spot operational anomalies in your environment and remediate them before they become institutional issues. For example, we worked with an organization that outsourced their Internet firewall management. When the supplier "cleaned up" some rules, they inadvertently disconnected their endpoints from the local management console, which also prevented propagation of the policies. Had the endpoint security team not been tracking these metrics, they would have only known about the changes upon encountering an operational issue, or worse a cyber incident.

